Managing your overall security position can feel like a daunting task. When looking at something as complex as Microsoft 365 (M365), it can be hard to understand all the bits and pieces that go into securing your organization and how to effectively use them. To manage this more effectively and achieve a strong security posture, it’s important to look at 3 key pieces to the puzzle: identity, data, and workspace. Bravo’s partner AvePoint describes each of these “layers” in their blog here. Let’s break each down even further to see how Microsoft will put you on the right path.
Identity Security
To begin, let’s look at what identity security is. Identity security allows you to manage accounts, roles, and entitlements for all applications, systems, data, and cloud service. The key place to start when looking at securing identity in your Microsoft environment is the Azure Active Directory (Azure AD). Azure AD houses many of M365 security capabilities that contribute to the security posture of your organization. Azure AD features one of the most important keys to securing identity — conditional access. Conditional access is used to control permission to a certain entry point. Microsoft describes conditional access as bringing signals together in order to make decisions and enforce organizational policies.
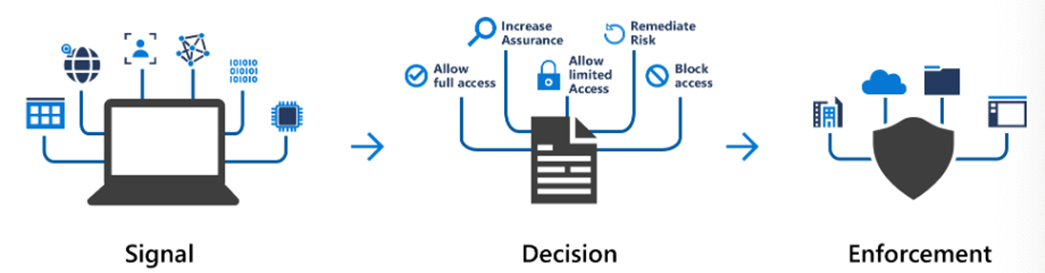
With this, Microsoft will require multi-factor authentication for administrators to be able to access various resources. Multi-factor authentication is a simple, yet effective, process to strengthen your security position. Microsoft describes two main goals for administrators when looking at conditional access:
- Empower users to be productive wherever and whenever
- Protect the organization’s assets
AvePoint also describes that device management, which is a conditional access policy, can be set up so unmanaged devices are blocked from having access to certain organizational resources. Conditional access helps protect against people having access to documents and applications they aren’t cleared for, which helps ensure data and documents won’t accidentally be leaked. These policies for securing identity not only help your overall security posture, but also work to keep you compliant with regulations such as FINRA and ITAR. However, this is only one piece of the puzzle when it comes to achieving strong M365 collaboration security.
Data Security
In order to secure your organization’s data, it’s crucial to understand why it should be protected. Your data is the heart of any organization. It is sensitive information, important documents and logs, and all things you wouldn’t want leaked. Data security focuses on protecting this information to prevent unauthorized access which can lead to data loss. Additionally, data security seeks to secure data against ransomware attacks, or any cyber-attacks that will modify or corrupt your data. Ponemon Institute’s Cost of Data Breach Study found that:
“On average, the damage caused by a data breach in the USA was $8 million. 25,575 user accounts were impacted in the average data incident, which means that beyond financial losses, most incidents lead to loss of customer trust and damage to reputation.”
This brings us to idea of Data Loss Prevention (DLP), which is one of the main ways Microsoft ensures your data is protected. DLP prevents users from inappropriately sharing data with people who shouldn’t have it. Creating a DLP policy is useful in identifying, monitoring, and automatically protecting sensitive items across all Microsoft services. But you don’t need to be an expert on different global data security regulations, this is where Microsoft has you covered with 300 predefined sensitive information types to help identify critical data. Microsoft is able to detect these sensitive items using deep content analysis and machine learning algorithms along with other methods to detect content that matches the DLP policies your organization creates. Additionally, Microsoft applies sensitivity (or document) labels which is a security feature where metadata is written into a document and goes with it as it moves. This not only simplifies securing your data, but ensures it’s protected wherever it goes.
Workspace Security
There is still one missing piece of this puzzle, and that is securing your workspace. Especially in today’s unique working environment with remote and hybrid, securing your workspace is an often-overlooked step that can greatly affect your overall security posture. M365 has a variety of tools to ensure a productive and secure environment, but it is ultimately up to the organization to ensure proper controls are set. AvePoint describes this best when they state: “If you apply protections and control to your whole workspace, you can be sure that your documents are secure even if there is no configuration made on an item-level.”
The most important aspect of securing your workspace is governance. Governance is the foundation for a strong company by creating a process for decision-making, accountability, control, and behavior. Governance helps secure a workspace by defining roles and responsibilities for an enterprise, this helps with securing data and infrastructure. It ultimately helps to mitigate risk by implementing policies to determine where the risk is coming from and keep your business compliant with government laws and regulation. However, governance is a broad topic and can be applied to a variety of areas. To learn more about enterprise, cloud, and development governance read our previous blog here.
Wrap-Up
All in all, Microsoft 365 provides a solid foundation for securing identity, data, and workspace. Microsoft works to simplify this process for you so that it is easily manageable. Ensuring these 3 key pieces of the puzzle are taken care of will contribute to the success of your organization’s security posture. The good news is Bravo has partnered with AvePoint to help you through the entire process.
Interested in making the switch to Microsoft 365 and/or need help securing your environment? Fill out the form below to get in contact with one of our experts!