If you haven’t yet considered adopting a Zero Trust security strategy, then now is the time! Zero Trust is an essential part of an organization’s security plan. It follows the motto: “Never trust, always verify.” This means that with a Zero Trust security plan, anyone or anything inside or outside the firewall will not automatically be trusted. However, a strong Zero Trust policy will not happen overnight… It takes time to fully implement it into an organization. Zero Trust is a set of processes, rather than a single solution. Given this, it is necessary to implement controls and technologies across all foundational elements: devices, applications, data, infrastructure, and networks. Let’s examine 5 key adoption strategies to consider when looking at Zero Trust.
Use Identities to Control Access
One of the first strategies we recommend is to use identities in order to control access. Identities are made up of the people, services, and IoT devices in your organization. They’re a powerful way to control access to data and serve as a common denominator across networks, endpoints, and applications. Microsoft describes this as:
“When any identity attempts to access any resource, security controls should verify the identity with strong authentication, ensure access is compliant and typical for that identity, and confirm that the identity follows least privilege access principles.”
It’s important to define the source of truth for identity and what other identity sources they might associate with. Something that can help with this is monitoring application access by removing stale entitlements that are no longer required. This could be due to role changes, departures, contract terminations etc., but whatever the reason, it’s crucial to keep an eye on this. Furthermore, you should establish when strong authentication is required.
Evaluate Authentication
This leads us to the next important Zero Trust adoption strategy – evaluate authentication methods. This involves incorporating multi-factor authentication or continuous authentication to improve said identity management strategy. This drastically can improve an organization’s overall security position. It does so by concealing applications from being fingerprinted, port scanned, or probed for vulnerabilities. On top of this, it evaluates signals from applications, users, and data to monitor risk. Using continuous authentication capabilities will give an organization the ability to validate identity when a user’s IP address or routine behavior pattern changes.
One other way to evaluate authentication is by incorporating passwordless authentication. This replaces a traditional password with two or more verification factors and is secured with a crypto key pair. When an organization registers this, the device creates a public and private key. Private keys can be unlocked via PIN or biometric authentication. This promotes simplicity and security. Another capability of keys is encrypted messages. These encrypted messages contain digital signatures that provide an additional means of verifying info and senders. There are two types of encryption: symmetric and asymmetric. Symmetric encryption is the faster method as only one key is utilized. Despite this, asymmetric encryption is the more secure and scalable option for larger organizations. This is due to the fact that the user will never be forced to reveal their private key to anyone and their public key will be accessible to those who need it. The following depicts a good example of asymmetric encryption.
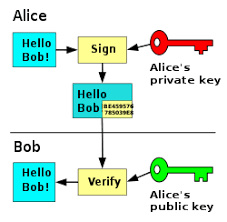
Something important for organizations to remember is that these authentication measures should be easy and transparent. You want your data to be secure while also considering the endpoint and end user. Something to help with this is increasing and decreasing the use of strong authentication depending on whether risk is higher or lower.
Segment Corporate Network and Applications
Zero Trust is all about protecting critical business data. Therefore, it is necessary to segment networks since this business data is accessed over network infrastructure. These networking controls provide critical functionality to enhance visibility as well as prevent attackers from moving laterally across the network. On-demand isolation can help with this. This is isolation that automatically inserts itself during conditions of high risk. It constrains the blast radius of compromised users and of dangerous or risky websites. The biggest thing with segmentation is protecting your internal facing assets. Internal facing assets are critical to the functioning of an organization. This would be your web server or email server, essentially where all your network traffic travels internally. Proper segmentation can also improve performance as local traffic becomes minimized.
In addition to network segmentation, application segmentation is just as important. Application segmentation applies when you employ third party apps, such as an Identity and Access Management tool. Organizations should work to find a balance between providing access to and maintaining control of applications to ensure the data they contain is secured. There are a few strategies to help with this:
- Apply controls to discover shadow IT
- Ensure appropriate in-app permissions
- Gate access based on real-time analytics
- Monitor for abnormal behavior
- Restrict user actions
- Validate secure configuration options
Following these strategies is a key step in implementing a solid Zero Trust policy.
Secure Your Devices
More than anything, you want to ensure your devices are secure. This could make or break a Zero Trust strategy. Something often forgotten is that the same security policies should be applied whether the device is corporately owned or personally owned. If this device is accessing corporate network, it can put your organization at risk if it is not fully secure. Ensure corporate, contractor, partner, and guest devices are treated the same. In addition, define overall differentiation for data access from managed and unmanaged devices. Add adaptive policy details to access content based on context.
There are a variety of ways to create a corporate device policy. The first way is BYOD– Bring Your Own Device. BYOD policy allows you to access business assets, but brings up the risk of employees not acting accordingly. Another way is CYOD– Choose Your Own Device. CYOD means the company provides the device, but employees have a choice in it and configure them. Additionally, there is COPE– Company Owned Personally Enabled. COPE is an improved version of BYOD, but a similar idea. Lastly, there’s COBO– Company Owned Business Only. COBO puts all control to the company which is great for security purposes. Regardless of the path an organization chooses to go with, security should be at top priority.
Define Roles and Access Controls
Lastly, control which users have access to which apps and services. This requires organizations to make sure roles are clearly defined. Additionally, once these roles are defined, the defined role must be managed. This is something you must think of when defining the roles so that managerial issues don’t occur. Classifying user personas and levels of access within your organization will help with creating these roles. However, you also must inventory all applications and identify all company assets. When you have this big picture to look at, it simplifies the process of deciding which roles have access to what data. Once this is done, you can evaluate authentication for each role and decide how at risk each application and role is. After this is implemented, an organization must contrast, maintain, and monitor a database that maps users (employees and third parties) to applications.
According to our partners at AvePoint, “Delegated administration can also serve as a security best practice, allowing whoever owns the information to manage their own data. This is particularly helpful for agencies working with sensitive data who are often mandated to only allow the team that owns the data to know it exists.” To learn more about delegated administration, check out their blog here.
Wrap-Up
Overall, Zero Trust serves to put your organization in the best security position possible by assuming breach and verifying each request as if it originates from an uncontrolled network. While it is a newer concept, Zero Trust is becoming more and more crucial for companies to begin adopting. As stated before, it is not a one and done process. There are a number of steps and processes to consider when implementing Zero Trust. That’s why we recommend contacting a trusted partner, like Bravo & AvePoint, to do the heavy lifting for you. Bravo has 12+ years of proven experience delivering AvePoint solutions to federal agencies to help strengthen their security posture and achieve compliance. By pairing AvePoint’s Zero Trust Solution with our implementation and Adoption & Change Management services, we can help you adopt Zero Trust in a simple and streamlined manner.
Interested in learning more about Zero Trust and how we can help? Fill out your information below to get in contact with one of our experts!











