February 24, 2022, marked the beginning of a war between Russia and Ukraine as Russia initiated a full-scale invasion of Ukraine. As tensions continue to escalate, the United States and other NATO nations impose sanctions on Russia. These sanctions are a result of the actions done by Russian president, Vladmir Putin. With more U.S. involvement in the war, it is crucial to be cautious and prepared for any Russian cyberattacks that may take place. So far, there have been no cyberattacks outside of Ukraine that should cause panic. While experts are puzzled as to why Russia has not attempted any damage yet, they urge people to remain vigilant of what might come.
Successful Russian Attacks So Far
The first cyberattack believed to be backed by the Russian government was seen in 2007 in Estonia. Since then, Russian cybergroups have been responsible for numerous damaging attacks in different countries. A recent example in U.S. news was the SolarWinds attack. This attack impacted 18,000 of its customers including U.S. agencies and private companies such as Microsoft and Cisco. Furthermore, the Russian government also backed various attacks in Ukraine over the years. Most recently, a data-wiper malware, known as HermeticWiper, hit Ukraine at the start of the Russian invasion. Data-wiper malware is software that can destroy large amounts of data with no detection.
Kyiv parliament, government, Foreign Ministry and other state institutions’ websites became inaccessible the day Russian groups invaded Ukraine. The hackers implemented a distributed denial-of-service attack (DDoS). When this happens, the servers are flooded with illegitimate requests. This causes the infrastructure to become overwhelmed and crash. This is when Ukraine also found the data-wiper malware on their computers. Russia launched a similar cyber attack in 2017 against Ukraine. This has led Ukraine to believe that this recent attack came from Moscow.
Who Is At Risk
Without a doubt, the risk of a cyberattack is highest for Government agencies, contractors, and those in the Defense Industrial Base (DIB). Secondly, critical infrastructure, such as energy, water, and hospitals, are also at a high risk. The Critical Infrastructure Defense Project has been created to help protect these services by offering free services. Lastly, another sector at risk is financial institutions. These sectors are at the greatest risk because they hold critical information and perform necessary services to the United States.
At this time, the threat to citizens is low, but citizens could be affected by phishing and disinformation. So far, a phishing campaign targeting those wanting to support Ukraine has been seen. Emails urging people to “help Ukraine” are guiding people to links as well as false Bitcoin and Ethereum addresses. The phishing emails may appear legitimate, including Ukraine addresses or looking as though they are from popular news sources. With Ukraine already raising $37 million in cryptocurrency donations, it can be difficult to tell which sites, links, and addresses are legitimate. Be sure to do research on where your money is going if you choose to donate.
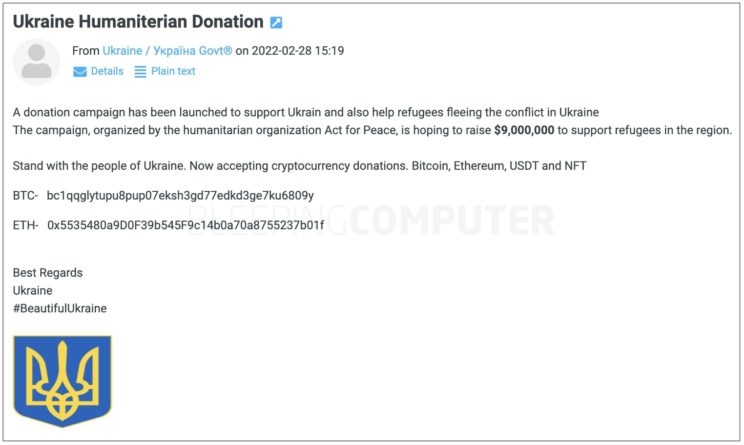 “Help Ukraine” phishing email pretending to come from npr.org. From https://www.bleepingcomputer.com/news/security/help-ukraine-crypto-scams-emerge-as-ukraine-raises-over-37-million/
“Help Ukraine” phishing email pretending to come from npr.org. From https://www.bleepingcomputer.com/news/security/help-ukraine-crypto-scams-emerge-as-ukraine-raises-over-37-million/
What We Might See
“Russia and other nation state threats continue to push and test the boundaries with both private and public sector organizations in the United States. We see cyber attacks only get more sophisticated and aggressive with the United States Defense Industrial Base (DIB) backing Ukraine and imposing sanctions crippling the Russian economy.” – Collin Kubal, Cybersecurity Manager at Bravo Consulting Group, LLC.
Along with phishing attacks, the spread of disinformation can be damaging to companies and governments. To stay well-informed on what news is factual, check out the Department of State’s fact sheet . In addition to direct attacks and disinformation, we may also see a “spillover” from attacks targeting different countries. An example of this is the Russian government’s malware called NotPetya. NotPetya was a malware that accidentally spread from Ukraine to other countries. The total damage of it was about $10 billion worldwide.
Something else important to note is that large companies, such as Microsoft, Apple, and Google are taking a stand to minimize the damage of the Russian government. Companies like these are stopping sales in Russia, offering extra services to businesses in Ukraine, and attempting to stop the spread of disinformation. Microsoft’s recent blog talks about what they are doing to help those in need.
What You Should Do
When it comes to cybersecurity attacks at this scale, it is critical that you ensure your organization’s cybersecurity practices are up to standard and that you stay up to date with official news.
- CISA: Stay up to date with Cybersecurity & Infrastructure Security Agency (CISA)
- CMMC: For Government contractors, the Cybersecurity Maturity Model Certification (CMMC) was created to help protect the nation from cyberthreats. Getting everything prepared to become certified, when able to, will help mitigate risk to your organization.
- Zero Trust: Implementing Zero Trust in your organization will help stop threats before they can cause damage. Read our free whitepaper, Zero Trust and the Impact to Your Organization, for how to get started.
For more cybersecurity tools your organization should consider implementing, check out our blog, “What Should You Budget For in 2022?“
How We Can Help
Bravo has 14+ years of experience delivering innovative business intelligence and digital transformation solutions to the federal government, intelligence community, and private sector. If you are a Government contractor in need of help with CMMC or a federal agency or organization interested in adopting Zero Trust, Bravo Has Your Back.
Fill out the form below to get in contact with one of our cybersecurity experts!











