As the world starts to transition into a “new normal” after the Covid-19 pandemic, it is time to look at how this impacts our workdays. According to a Gartner survey, 82% of companies are allowing their employees to partially work remotely. This hybrid work model is becoming popular as many employees are not willing to sacrifice their freedom of working from home. Although it is convenient for most, remote work has made an impact on the security of organizations. Phishing and ransomware have increased as people work on devices not protected by their organization’s security.
Although bringing willing employees back into the office will be beneficial for company culture, security leaders will now have to juggle managing security in-office along with remote work. As more organizations adapt to hybrid work, security will also have to adapt. Furthermore, transitioning to a hybrid environment also helps pave the path to digital transformation. Thus, the focus now is on ensuring that your hybrid workplace can stay secure.
Here are some aspects of hybrid work that require a focus on security and ways to make your hybrid work environment successful.
Where to Focus Security
The Cloud
Firstly, strong cloud security is essential for a successful hybrid work environment. Currently, Microsoft Azure, Amazon Web Services (AWS), and Google Cloud are the top cloud service providers. Service providers come with their own suite of security tools that cover the basics. However, when dealing with more complex cloud environments, organizations are more secure with third-party services.
With today’s cyber threats existing, your organization needs more security than ever. Using a third-party security consultant, like Bravo, is a must. Bravo can assess, harden, and future-proof your environment so you can stop threats before they happen. Therefore, you can make the most out of your cloud investment. For instance, Bravo helps customers navigate Microsoft Azure’s security services to maximize your security posture. To learn more about cloud security, read our blog partnered with AvePoint, Collaborate Securely in the Cloud.
By migrating to the cloud, you can optimize your time and resources to get things done more efficiently. Besides increased security, another benefit of the cloud is being able to pay as you go. As your organization grows, your cloud environment can as well. Collaborating with coworkers in the cloud is also now easier than ever. With Microsoft Teams’ new hybrid integrations, working remotely is no longer a disadvantage.
Still unsure about the cloud? Check out our blog, Migrate to the Cloud in 2022, for benefits and why you should make the switch now.
In a hybrid work environment, email is another great collaboration tool to keep everyone in the loop. But with over half of phishing attacks directly leading to ransomware, email security should be a priority for every organization. Have no fear! Security providers, like Bravo, can implement spam/phishing blockers to help keep your organization safe from attackers. A banner letting you know that a sender is outside of your organization can be a life saver in phishing attempts. There are also tools that automatically block an email from coming through and let you review it safely.
In-Office Security
Although cybersecurity is extremely important for hybrid work, we cannot forget about dangerous in-person scenarios. Threats with access to the office can lead to threats online. Be sure that your organization is tracking visitors and keeping on-site data secure. The safety of locking doors and cabinets and logging out user credentials is still as important as ever.
How to Ensure Security
Zero Trust Security
Implementing Zero Trust security is practically a requirement for hybrid work environments. As the new “golden standard” of cybersecurity, it is essential to managing devices and users in various locations. Zero Trust’s motto of “Never trust, always verify” means that each user/device needs to be authenticated to grant access. Keep in mind that Zero Trust is not a tool your organization can buy and install. Instead, it is a mindset and collection of combined practices to create an impenetrable environment. Because of this, its implementation will look different for every organization.
Two of the most standard tools used in a Zero Trust framework are multifactor authentication (MFA) and least privileged access.
- Multifactor Authentication: MFA is essentially a password-less authorization from a device that only you have access to. For example, when logging into your email in a web browser, your cell phone will get a notification that you must approve before logging in.
- Least Privileged Access: Granting users least privileged access allows them to get the information they need without giving them access to other important data. In the case of a breach using this user’s credentials, more important data will automatically be inaccessible.
For a more in-depth look at the Zero Trust model, read our whitepaper, Zero Trust and the Impact to Your Organization.
On the contrary, a tool that is starting to become more of a hassle than help is a virtual private network (VPN). VPNs are used to encrypt data from the corporate network to the user. Although this can be helpful, it is another point that can be tampered with by cyber threats. When using a VPN, you are still at just as much risk, if not more, of encountering bots, malware, viruses, etc. and transmitting them back to the corporate network.
Check out some of our recent blogs about Zero Trust:
Backups
One of the most common things Information Technology (IT) leaders focus on is data loss prevention. That is what backups aim to resolve. Simply put, backups are like insurance for your files, whether in the cloud or on-prem. In a hybrid work environment, ensuring every employee’s data is being backed up will save money and important data, especially in the case of a ransomware attack. Backing up your files is also helpful when files are accidentally deleted or cannot be found.
Training
Last, but certainly not least, is preparing employees to operate securely in a hybrid work environment. Since cybersecurity is everyone’s responsibility, providing proper training is important to keeping the entire organization secure. Below are some ways to increase cybersecurity knowledge amongst in-person and remote workers:
- Simulations: Creating fake phishing emails to send to employees is a clever way to test their knowledge and help them understand what to look out for.
- Modules: Quick modules that explain the impact of phishing, ransomware, and overall importance of cybersecurity are an effective way to stay fresh on the latest cybersecurity trends.
- Security Newsletters: Sharing current cybersecurity news will help emphasize the need for everyone to do their part. Although sharing statistics and the impact of cyber attacks can be frightening for employees not used to cybersecurity practices, it can help them visualize how important doing their part is.
- Increase Password Knowledge: Have employees ensure their passwords are up to standard by using a chart like the one provided below. Even better, using a password manager allows employees to create complex passwords for each different account to decrease risk of a breach.
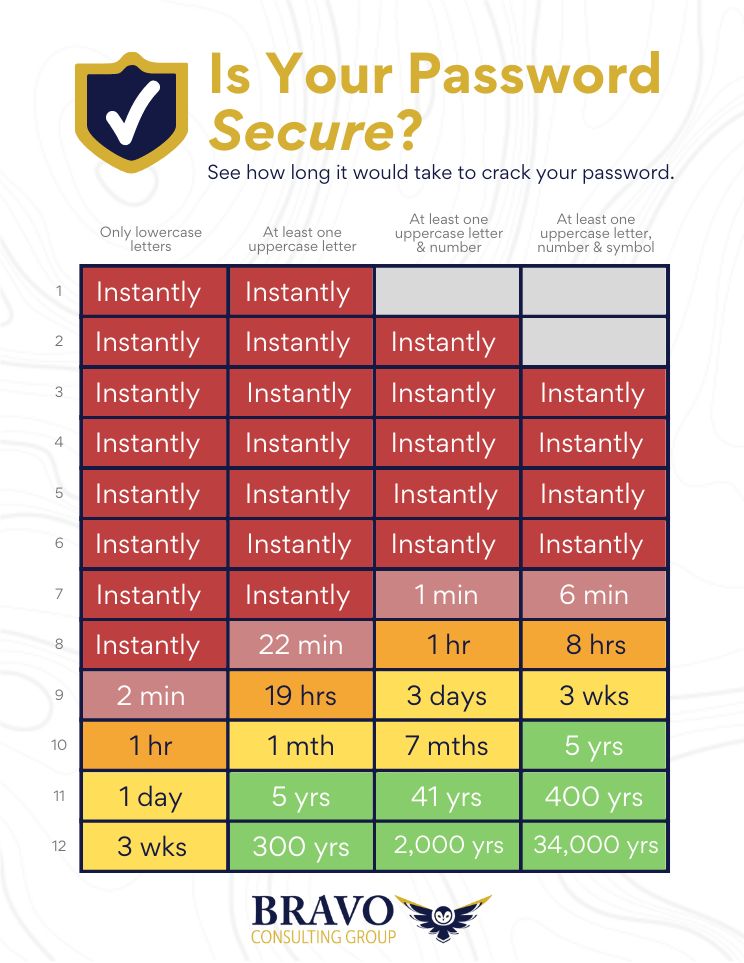
Need help creating passwords? Check out our infographic on creating the perfect, un-hackable password!
All-in-all, creating a successful hybrid work environment requires tight security in many different areas. Ensuring your cloud, emails, and in-person data is secure is nonnegotiable. By having a strong backup solution, training employees, and implementing a Zero Trust security framework, your organization is closer to sustaining hybrid work for years to come!
If you have any additional questions, need help with an on prem to hybrid migration, or need help securing your hybrid work environment, Bravo has your back! Fill out a form below to get in touch with one of our security experts!




